When Cybersecurity Becomes Your Competitive Advantage
Date
Investing in data privacy and cybersecurity can eliminate one of the biggest barriers to adoption by most school districts.
You’ve probably noticed procurement conversations with school districts are shifting. Where districts once focused primarily on learning outcomes and ease of implementation, they’re now asking harder questions about data protection, compliance certifications, and vendor security practices.
They have good reasons. According to a recent report from the Center for Internet Security, 82% of schools experienced cyber threat impacts over 18 months, with districts facing an average of five cyber incidents per week. The PowerSchool breach—potentially exposing 50 million students’ personal information—has made “cybersecurity requirements” a non-negotiable part of every RFP.
As Doug Levin from K12 Security Information Exchange told Education Week: “Districts need to be clear about what their non-negotiables are for cybersecurity. That has to be done during procurement. It has to be an explicit evaluation criterion, and those requirements need to be enshrined in contract language.” And he’s not alone in advocating this.
CISA’s K-12 Digital Infrastructure Brief makes a similar point: “Vendors and service providers play an outsized role in the privacy, security, accessibility, and interoperability of K–12 digital infrastructure.” They’re not just suggesting compliance—they’re expecting it.
Navigating the Compliance Landscape
Understanding which standards apply to your situation can help you make strategic investments in the right places: Essential first step:
NIST CyberSecurity Framework (NIST CSF)
The NIST CSF provides guidance for managing cybersecurity risks through a taxonomy of high-level security outcomes. Rather than prescribing specific tools, it offers flexible guidance on practices and controls that organizations can adapt to their context.
Why it works as a good first step: NIST CSF emphasizes risk management, communication across the organization, and ongoing monitoring. It offers a taxonomy of high-level security outcomes that can be used by any organization to understand, assess, prioritize and communicate its cybersecurity efforts. Rather than prescribing specific tools or methods for achieving outcomes, it provides guidance on practices and controls that could be used to achieve outcomes. Organizations may self-certify compliance, making it accessible for teams with limited resources.
Best for: U.S.-focused organizations looking to establish foundational security practices and demonstrate due diligence to school district customers.
For Competitive Differentiation: Service Organization Controls 2 (SOC 2)
SOC 2 focuses on security, availability, processing integrity, confidentiality, and privacy of customer data and systems. This compliance framework requires external auditor certification, adding third-party validation to your security claims. Look to see SOC 2 become the “gold standard” for edtech solutions in the years ahead.
Why districts care: SOC 2 provides independent verification of your security practices—exactly what risk-averse school administrators need to justify vendor selection decisions.
Best for: Technology services companies, especially SaaS providers, looking to differentiate in competitive procurement processes.
For International Markets: ISO 27000 Family
ISO 27000 is a family of standards meant to guide organizations in establishing, maintaining, and improving Information Security Management Systems (ISMS). ISO 27001 is the most recognized standard for ISMS. Other standards in the collection cover additional best practice in data protection and cyber resilience. Organizations achieve certification through accredited assessment bodies.
Why it matters globally: ISO 27000 provides internationally recognized credibility, essential for organizations serving diverse geographic markets or working with multinational education companies.
Best for: Larger organizations with mature security programs seeking global market access and enterprise-level credibility.
Additional Options
Secure Controls Framework (SCF): SCF is a “meta-framework”— a framework of frameworks— which focuses on internal cybersecurity and data protection controls. It is made up of over 200 authoritative sources (e.g. statutory, regulatory, and contractual frameworks), making it useful as a mapping tool between different frameworks. SCF is useful for medium to large organizations managing multiple compliance needs simultaneously.
CIS Critical Security Controls: CSC are prescriptive, prioritized best practices that align with NIST CSF. Provides specific actions that can be mapped to broader framework requirements.
CoSN K-12 Community Vendor Assessment Tool (K-12CVAT): Not a compliance standard, but a questionnaire framework school districts are using to measure vendor risk. Understanding K-12CVAT helps you prepare for common school district security evaluations. It is a good starting point for getting familiar with the breadth of cybersecurity and data privacy practices schools are expecting vendors to disclose before purchasing.
How We’re Approaching This Reality
Clarity implemented NIST CSF three years ago and is in the process of upgrading to CSF 2.0 and preparing for SOC2 certification in the near future. The combination of both keeps us focused on the future while protecting your and your customer’s data entrusted to us. Here’s some examples of what that looks like in practice:
- Multi-factor Authentication (MFA) is in place across systems
- The principle of least access is used across all systems to grant users access to internal and client resources, and is managed centrally in our identity & access management (IAM) system
- Vulnerability scans are regularly performed against our systems and client applications we host
- Our staff takes an annual security awareness training course to refresh their knowledge and learn about emerging threats
- Our Infrastructure and Engineering teams actively monitor and act on security releases for component software used for internal and client systems
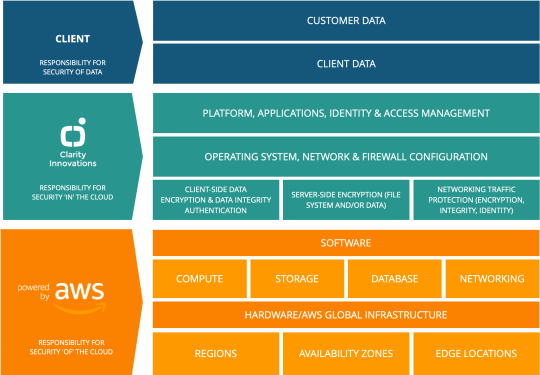
We also leverage Amazon Web Services’ shared responsibility model to clarify security domains:
- AWS handles data center and infrastructure security;
- Clarity manages operating system and application security; and,
- Our clients have responsibility for user security and customer data they collect.
What Cybersecurity Means for Your Product Strategy
The cybersecurity landscape isn’t just changing—it’s reshaping procurement requirements, contract negotiations, and competitive positioning. These certifications have become prerequisites for adoption in most large school districts across the country. Organizations that get ahead of this trend will find themselves with significant advantages over those that don’t.
Lost Revenue: Districts are increasingly eliminating vendors from consideration based solely on security posture, regardless of product quality or learning outcomes. Your best solution won’t matter if you can’t clear the security hurdle.
Competitive Differentiation: Organizations with robust compliance frameworks are winning deals against competitors that have traditionally prioritized instructional value over data privacy and security.
Resource Allocation Challenges: The struggle between feature development and paying down technical debt is now more challenging with compliance requirements in the mix. The question isn’t whether to invest in cybersecurity—it’s how to do it efficiently without compromising innovation.
It’s Not About When, But What…And We Can Help
Overall, the question isn’t whether you need to prioritize cybersecurity compliance—it’s deciding on which certifications will give you the competitive edge needed and how quickly you can implement them without derailing your product roadmap.
The organizations winning in today’s market aren’t just building better products—they’re building products that districts can confidently adopt. Based on current trends, we expect SOC 2 certification requirements to become increasingly common as states and districts seek stronger third-party validation of vendor security practices.
We’ve helped dozens of clients navigate these exact challenges, from compliance strategy to implementation support. Contact us today to learn how we can help you navigate the challenges of hardening the cybersecurity and data privacy protections within your edtech solution.

