Managing Technology Infrastructure to Anticipate the Future
Date
Hundreds of things that can go wrong with technology. Here’s our recipe for keeping your educational solution stable, secure, and scalable.
Your edtech product roadmap depends on infrastructure that just works. But when was the last time you thought about what ‘just works’ actually requires? It means orchestrating a complex symphony of services, security measures, and continuous monitoring and analysis. Here’s what really goes into keeping these mission-critical systems running smoothly.
The Infrastructure Pie
Modern cloud infrastructure provides managed database services, scalable storage, server-less computing capabilities, secure API gateways, and content delivery networks that ensure fast load times everywhere.
What does it take to maintain the myriad of moving parts that constitute edtech infrastructure? We recently analyzed where our infrastructure and engineering teams invest time across a typical year. The results reveal just how multifaceted this work really is:
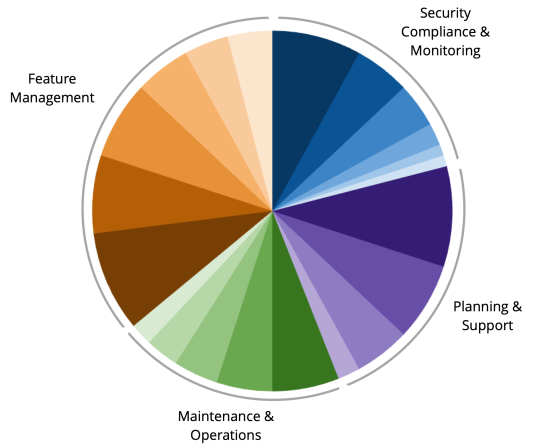
Feature Management (36% of effort): Building new capabilities, enhancing existing features, addressing accessibility, and planning feature definitions represents nearly a third of our work. This isn’t just about adding functionality—it’s about architecting solutions that scale, perform, and integrate securely with the broader system. When edtech infrastructure is architected thoughtfully from the start, features ship faster because they’re built on solid foundations rather than working around technical debt.
Maintenance and Operations (20% of effort): This category happens behind the scenes—bug fixes, scaling and performance optimization, refactoring code for maintainability, testing and quality assurance, and managing the dependency upgrades, DevOps processes, and required migrations that keep systems current and secure. This effort is what prevents the 2:00 am emergency calls that derail your release schedule. It’s what keeps your product stable during peak back-to-school season. Consistent maintenance means predictable performance.
Security, Monitoring, and Support (21% of effort): Security and compliance work combines with systems monitoring, penetration testing and vulnerability scans, incident research and analysis, and client support to ensure systems remain secure and responsive. This is what protects your company’s revenue and reputation. A single data breach can sink an edtech company—just ask any VP who’s had to notify districts that student data was compromised. This investment keeps you compliant with evolving regulations, maintains customer trust, and ensures your sales team never has to answer uncomfortable security questions they can’t address confidently.
Strategic Investments (23% of effort): Stability and scalability investments as well as sunsetting obsolete features represent the forward-thinking work that prevents problems before they occur. This is your insurance policy against the “success disasters” that plague growing edtech companies. When that large district or statewide deal gets signed, and suddenly you have 50,000 users hitting your system simultaneously, this investment is why your platform doesn’t buckle. It’s also what allows you to confidently enter RFPs that require specific performance guarantees.
Security and Privacy: Non-Negotiable Priorities
In K-12 education, we’re not just managing technology—we’re safeguarding sensitive student data. This responsibility shapes every aspect of our approach.
Processes First: Cybersecurity isn’t just about firewalls and encryption. It’s about building robust processes that become second nature—regular security audits, patch management protocols, access control reviews, and incident response plans. Every system update, every configuration change, and every new integration goes through our internal security review process.
Data Privacy by Design: Educational applications must comply with dozens of federal and increasingly complex state-level privacy laws. We help clients navigate and comply with Data Privacy Agreements required by their customers, translating legal requirements into technical controls and operational procedures. This isn’t a one-time checkbox—it’s an ongoing partnership that evolves as regulations change. For example, in our work with Family Engagement Lab, we spent a sprint implementing robust logging of security events such as user logins and admin masquerade to comply with one large customer’s requirements.
Automation, Monitoring, and the Pursuit of Performance

Manual infrastructure management doesn’t scale, and it introduces risk. That’s why automation is woven throughout our operations—from configuration management that ensures deployments are identical and repeatable to automated backup processes that provide reliable recovery points. Our DevOps practices enable us to deploy updates safely and efficiently.
But automation is only part of the equation. Continuous monitoring provides the situational awareness needed to maintain healthy systems. We track performance metrics, server health, application errors, and security events in real time. We measure infrastructure and application performance telemetry, and network traffic to alert us when something deviates from expected norms. This allows us to respond quickly, before issues affect the user experience.
Meeting performance standards isn’t aspirational; it’s operational. We methodically evaluate and choose the right tool for the job. For one database-intensive application, we deployed an auto-scaling database to handle traffic ebbs and flows. But we didn’t stop there—we implemented an automated database bump to warm it up for the US school day. Then, at the end of the day when traffic is lower, we saved the client money by scaling it down. The effort we invest in scaling and performance optimization ensures applications remain responsive as usage grows and evolves.
The Work You Don’t See
The best edtech infrastructure is invisible—systems that work so reliably that users don’t think about them at all. That invisibility, however, requires visible expertise, constant vigilance, and a commitment to getting hundreds of small things right every single day.
Behind every smooth user experience, every fast page load, and every secure transaction are many distinct areas of effort our team manages continuously. Some, like feature development, are obvious. Others, like system monitoring or scaling, work precisely because they’re invisible to end users.
But here’s what makes this work truly strategic: every one of these efforts isn’t just about maintaining today’s systems—it’s about building infrastructure that’s ready for tomorrow’s challenges. When we invest in refactoring code, we’re creating a foundation that can adapt to new requirements. When we perform vulnerability assessments and install security patches, we’re taking proactive steps to protect client data. When we document our systems and automate our processes, we’re ensuring knowledge doesn’t become a bottleneck as teams and technologies evolve.
The educational technology landscape never stands still. New compliance requirements emerge, usage patterns shift, pedagogical approaches evolve, and technology capabilities expand. Infrastructure that merely maintains the status quo becomes a liability. Infrastructure that anticipates change becomes a competitive advantage.
Ready to talk about edtech infrastructure that adapts and anticipates your needs? Let's discuss how your product roadmap could benefit from partnership with our team. We handle today’s complexity while building tomorrow’s capability, allowing your customers to focus on what matters most: helping students learn and grow.


